Research
Our work has been supported by a portfolio of externally funded projects: three by the European Commission (EU FP7); four by the EIT ICT Labs; a Young Researcher Project award and a framework grant funded by the Swedish Science Foundation (VR); an Academy Fellowship funded by the a Knut and Alice Wallenberg, covering 10 years with its extension; a framework grant funded by the Swedish Foundation for Strategic Research (SSF); projects funded by the European Space Agency (ESA) and by the Wallenberg Autonomous Systems Program (WASP). Additional external funding: SRA ICT TNG, VINNOVA, EIT Digital, and Viktoria Swedish ICT. Below there are brief descriptions of several ongoing and recent projects, with few representative publications for each.
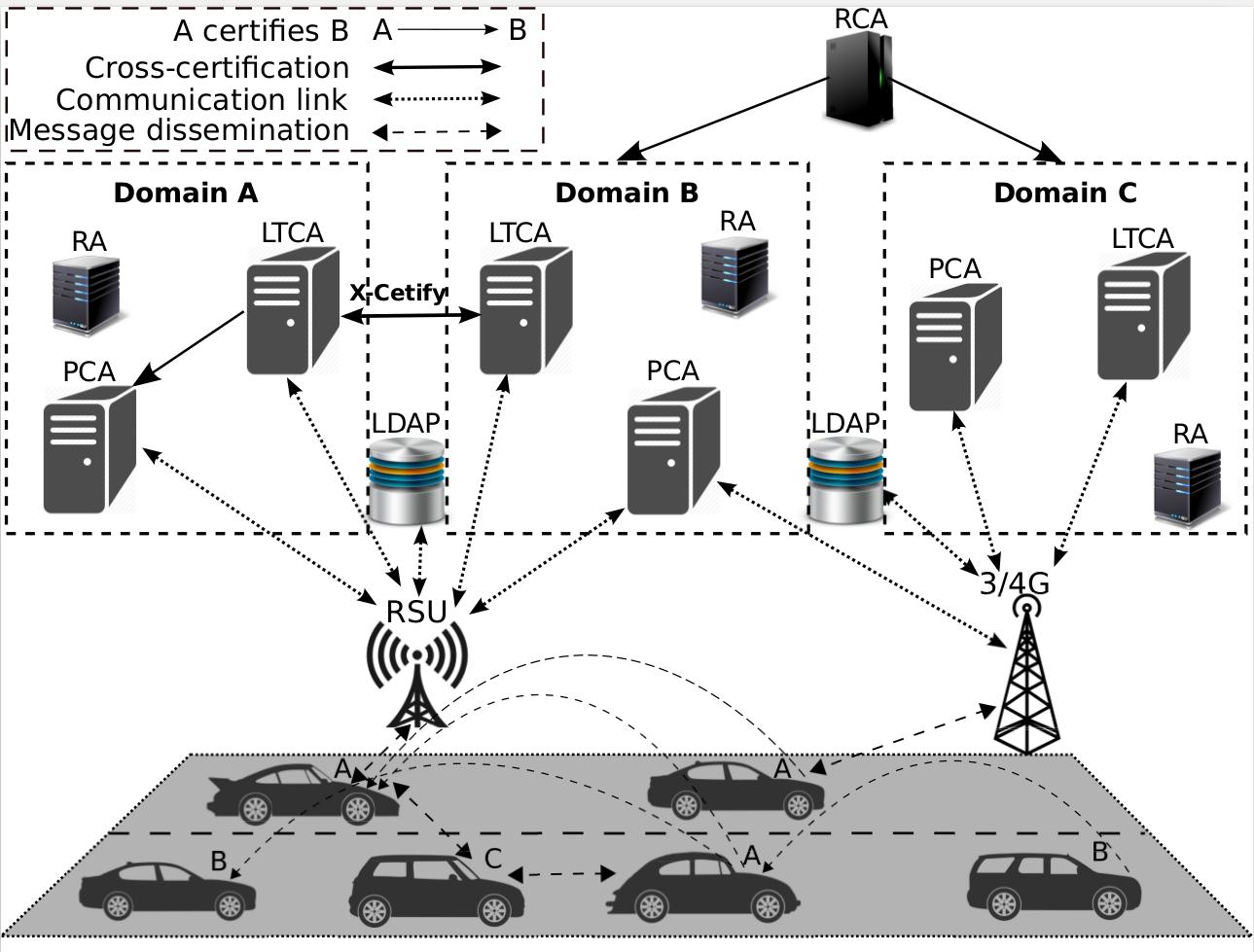
Credential Management for Emerging Large-Scale Networked Systems
| [1] | M. Khodaei, H. Norrozi, and P. Papadimitratos, “Scaling Pseudonymous Authentication for Large Mobile Systems,” in ACM Conference on Security & Privacy in Wireless and Mobile Networks (ACM WiSec), Miami, FL, USA, May 2019 [ bib | DOI | http ] |
| [2] | M. Khodaei and P. Papadimitratos, “Efficient, scalable, and resilient vehicle-centric certificate revocation list distribution in VANETs,” in ACM Conference on Security & Privacy in Wireless and Mobile Networks (ACM WiSec), Stockholm, Sweden, June 2018 [ bib | DOI | http ] |
| [3] | M. Khodaei, H. Jin, and P. Papadimitratos, “SECMACE: Scalable and Robust Identity and Credential Management Infrastructure in Vehicular Communication Systems,” IEEE Transactions on Intelligent Transportation Systems (IEEE ITS), April 2018. [ bib | DOI | Full Text ] |
| [4] | M. Khodaei and P. Papadimitratos, “Evaluating On-demand Pseudonym Acquisition Policies in Vehicular Communication Systems,” in ACM MobiHoc Workshop on Internet of Vehicles and Vehicles of Internet (ACM IoV-VoI), Paderborn, Germany, July 2016, pp. 7--12. [ bib | DOI | Full Text ] |
| [5] | P. Papadimitratos, L. Buttyan, T. Holczer, E. Schoch, J. Freudiger, M. Raya, Z. Ma, F. Kargl, A. Kung, and J.-P. Hubaux, “Secure Vehicular Communication Systems: Design and Architecture,” IEEE Communications Magazine, vol. 46, no. 11, pp. 100--109, November 2008. [ bib | DOI | Full Text ] |
Security and Privacy for Location Based Services
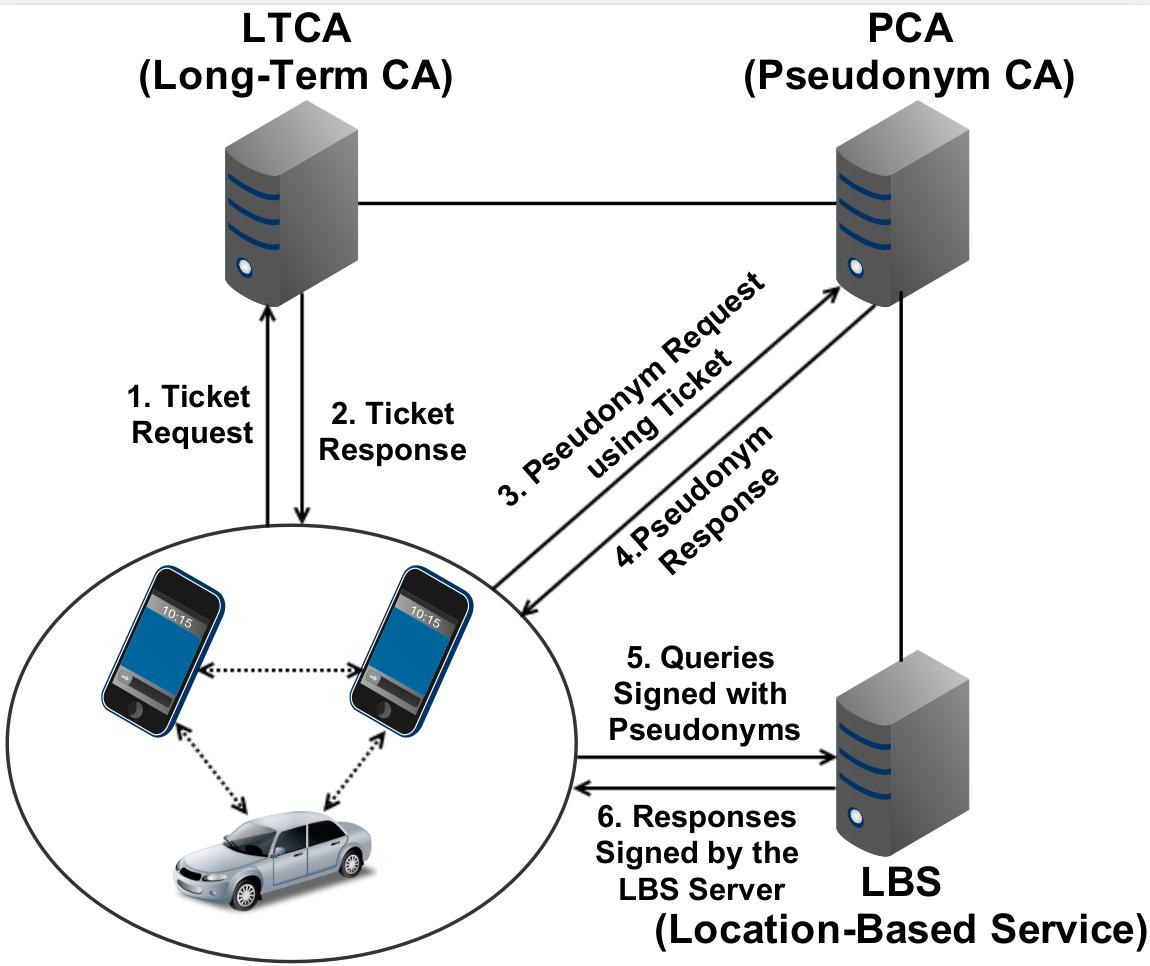
We have investigated how to protect the privacy of users of location based services (LBS) while ensuring the quality of service users receive. Our earlier work tackled the problem of honest but curious LBS: we challenged the traditional approach of relying on an anonymizer and brought forth caching and user collaboration as means to reduce significantly the user exposure to the LBS. Simply put, the fewer the queries submitted, the lower the exposure, as long as peers (other users) or local memory can provide timely responses. Our follow-up work addressed additional challenges and yielded a more versatile and resilient system.
Our system can effectively serve users that seek their personalized set of dynamically changing data, while it reduces dramatically the exposure to their honest but curious peers. More so, our system is highly resilient to malicious peers while it enhances privacy even against peers that collude with security infrastructure entities. We leverage our state of the art work on credential management. Other own related work focused on specific applications, notably intelligent transportation systems.
Representative publications
| [1] | H. Jin and P. Papadimitratos, “Resilient Privacy Protection for Location-Based Services Through Decentralization,” ACM Transactions on Privacy and Security (ACM TOPS), vol. 22, no. 4, pp. 21:1--36, December 2019. [ bib | DOI | Full Text ] |
| [2] | H. Jin and P. Papadimitratos, “Resilient Privacy Protection for Location-Based Services through Decentralization,” in ACM Conference on Security and Privacy in Wireless and Mobile Networks (ACM WiSec), Boston, MA, USA, July 2017, pp. 253--258. [ bib | DOI | Full Text ] |
| [3] | S. Gisdakis, V. Manolopoulos, S. Tao, A. Rusu, and P. Papadimitratos, “Secure and Privacy-Preserving Smartphone-Based Traffic Information Systems,” IEEE Transactions on Intelligent Transportation Systems (IEEE ITS), vol. 16, no. 3, pp. 1428--1438, 2015. [ bib | DOI | Full Text ] |
| [4] | R. Shokri, G. Theodorakopoulos, P. Papadimitratos, E. Kazemi, and J. P. Hubaux, “Hiding in the Mobile Crowd: Location Privacy through Collaboration,” IEEE Transactions on Dependable and Secure Computing (IEEE TDSC), vol. 11, no. 3, pp. 266--279, May 2014. [ bib | DOI | Full Text ] |
Security and Privacy for Participatory Sensing Systems

Building on closely related lines of research on S&P for LBS, VCS, and the design of security infrastructure, we have been working on securing participatory sensing - or mobile crowdsourced sensing - systems/applications. We designed an architecture for securing sensing systems and protecting contributors' privacy with data quality and user incentives as additional dimensions.
Our first paper on the topic received the best paper award of ACM WiSec. Our follow-up work addressed data trustworthiness, building on top of secure and anonymized yet accountable data collection, and providing, in addition, a means to evict wrong-doers; moreover, secure and privacy-preserving, fair user remuneration, and open user registration that mitigates sibyl-based misbehavior.
Representative publications
| [1] | J. Borsub and P. Papadimitratos, “Hardened Registration Process for Participatory Sensing,” Conference on Security and Privacy in Wireless and Mobile Networks (ACM WiSec), Stockholm, Sweden, June 2018 [ bib | DOI | Full Text ] |
| [2] | S. Gisdakis, T. Giannetsos, and P. Papadimitratos, “Security, Privacy, and Incentive Provision for Mobile Crowd Sensing Systems,” IEEE Internet of Things Journal, vol. 3, no. 5, pp. 839--853, October 2016. [ bib | DOI | Full Text ] |
| [3] | S. Gisdakis, T. Giannetsos, and P. Papadimitratos, “SHIELD: A Data Verification Framework for Participatory Sensing Systems,” in ACM Conference on Security & Privacy in Wireless and Mobile Networks (ACM WiSec), New York, NY, USA, June 2015, pp. 16:1--16:12. [ bib | DOI | Full Text ] |
| [4] | S. Gisdakis, T. Giannetsos, and P. Papadimitratos, “SPPEAR: Security and Privacy-preserving Architecture for Participatory-sensing Applications,” in ACM Conference on Security & Privacy in Wireless and Mobile Networks (ACM WiSec), Oxford, United Kingdom, 2014, pp. 39--50. [ bib | DOI | Full Text ] |
| [5] | ------, “Security, Privacy & Incentive Provision for Mobile Crowd Sensing Systems,” KTH DiVA Technical Report 181099, December 2015. [Online]. Available: http://urn.kb.se/resolve?urn=urn:nbn:se:kth:diva-181099 [ bib | Full Text | http ] |
| [6] | ------, “Data Verification and Privacy-respecting User Remuneration in Mobile Crowd Sensing,” KTH DiVA Technical Report 181098, December 2015. [Online]. Available: http://urn.kb.se/resolve?urn=urn:nbn:se:kth:diva-181098 [ bib | Full Text | http ] |
Secure and Privacy Preserving Vehicular Networking
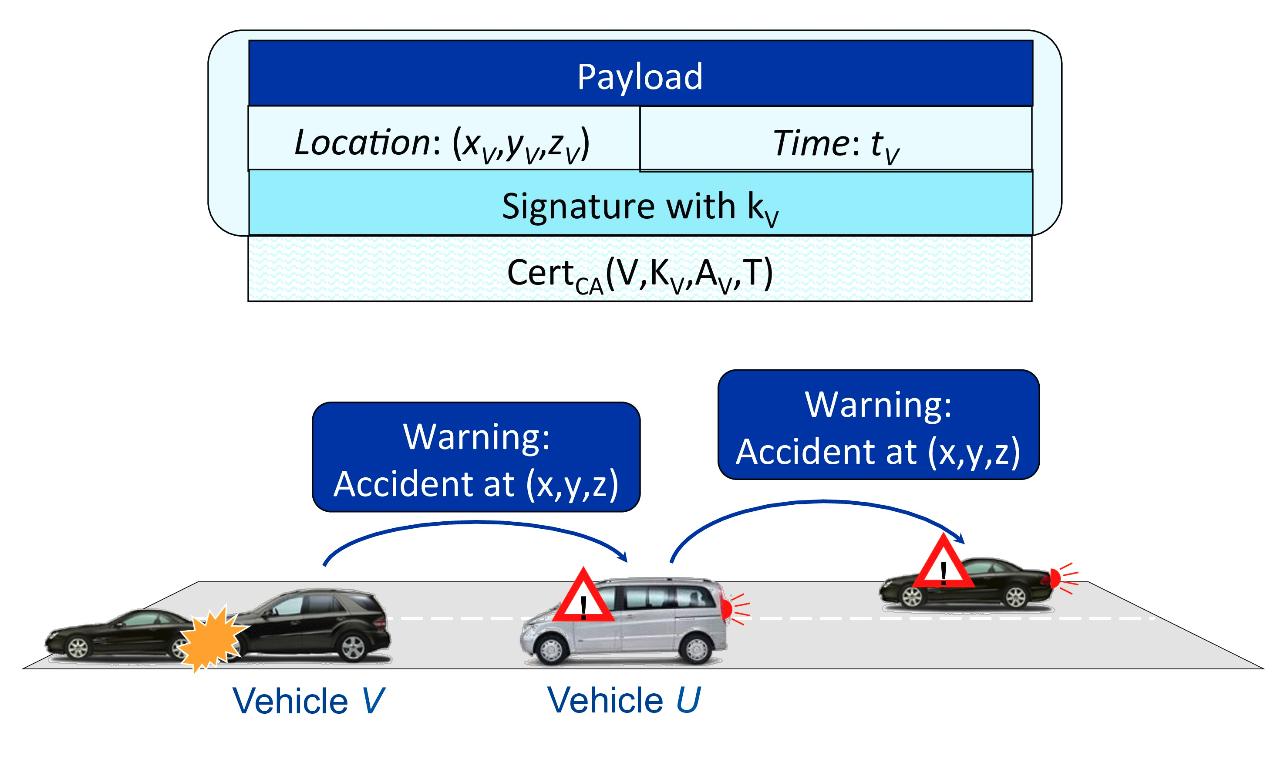
Vehicular communication systems (VCS) enable transportation efficiency and transportation safety applications, often with stringent requirements and dense networking environments. Security and privacy enhancing mechanisms, adding significant overhead, need to be highly efficient. More so, VCS need to remain resilient to clogging denial of service attacks, as well as function without compromising security or privacy even if access to the credential management infrastructure is interrupted.
We have addressed these challenges while seeking to preserve the VCS effectiveness, in terms of its baseline objectives, after adding strong security and privacy protection. In inverse chronological order, our most recent results include a highly efficient and resilient scheme for validating transportation safety messages - achieving low latency and high reliability under a clogging denial of service attack or in highly dense environments. Other results include schemes that effectively combine anonymous and pseudonymous authentication, enabling operation in the event of disconnection from the VPKI; continuing from an earlier work, the first to propose anonymous authentication primitives for VCS and evaluate the effect of security overhead on transportation safety.
Representative publications
| [1] | H. Jin and P. Papadimitratos, “DoS-resilient Cooperative Beacon Verification for Vehicular Communication Systems,” Elsevier Ad Hoc Networks, vol. 90, p. 101775, December 2019. [ bib | DOI | Full Text ] |
| [2] | H. Jin and P. Papadimitratos, “Resilient Privacy Protection for Location-Based Services through Decentralization,” in ACM Conference on Security and Privacy in Wireless and Mobile Networks (ACM WiSec), Boston, MA, USA, July 2017, pp. 253--258. [ bib | DOI | Full Text ] |
| [3] | G. Calandriello, P. Papadimitratos, J.-P. Hubaux, and A. Lioy, “On the Performance of Secure Vehicular Communication Systems,” IEEE Transactions on Dependable and Secure Computing (IEEE TDSC), vol. 8, no. 6, pp. 898--912, November 2011. [ bib | DOI | Full Text ] |
Secure Positioning

We have worked on securing positioning/localization, with a main focus on global navigation (GNSS)-based positioning for civilian applications. We have devised a number of countermeasures that can detect an attack, based on signal characteristics or inconsistencies due to the attack. For example, earlier work relied on time, power, doppler shift; the work resulted in a patent. More recent work has looked into weeding out spoofed or replayed signals, examining all available ones, possibly from multiple constellations. Overall, our work seeks to develop low-complexity software-based methods that detect attacks manipulating GNSS transmissions and thus prevent the use of faulty position information.
In this context, we have investigated sophisticated replay/relay attacks, as pointed out in our earlier papers.Those so-called distance decreasing attacks remain relevant even when GNSS signals are cryptographically protected, seeking to reduce individual pseudo-range measurements at the receiver. Related to the overall topic, in earlier work, we investigated secure ranging and distance bounding for Ultra Wide-Band (UWB) radios, as well as peer position verification in mobile networks.
Representative publications
| [1] | K. Zhang and P. Papadimitratos, "Secure Multi-constellation GNSS Receivers with Clustering-based Solution Separation Algorithm," in Proceedings of the IEEE Aerospace Conference 2019, Big Sky, Montana, March 2019 [ bib | DOI | Full Text ] |
| [2] | K. Zhang and P. Papadimitratos, "On the Effects of Distance-decreasing Attacks on Cryptographically Protected GNSS Signals," in Proceedings of the 2019 International Technical Meeting of The Institute of Navigation, Reston, Virginia, Jan 2019 [ bib | DOI | Full Text ] |
| [3] | P. Papadimitratos and A. Jovanovic, “Method to Secure GNSS-based Locations in a Device having GNSS Receiver,” April 2012, US Patent 8,159,391. [Online]. Available: http://www.google.com/patents/US8159391 [ bib | Full Text | http ] |
| [4] | P. Papadimitratos and A. Jovanovic, “GNSS-based Positioning: Attacks and Countermeasures,” in IEEE Military Communications Conference (IEEE MILCOM), San Diego, CA, USA, November 2008, pp. 1--7. [ bib | DOI | Full Text ] |
| [5] | ------, “Protection and Fundamental Vulnerability of GNSS,” in IEEE International Workshop on Satellite and Space Communications (IEEE IWSSC), Toulouse, France, October 2008, pp. 167--171. [ bib | DOI | Full Text ] |
Information Theoretic Security
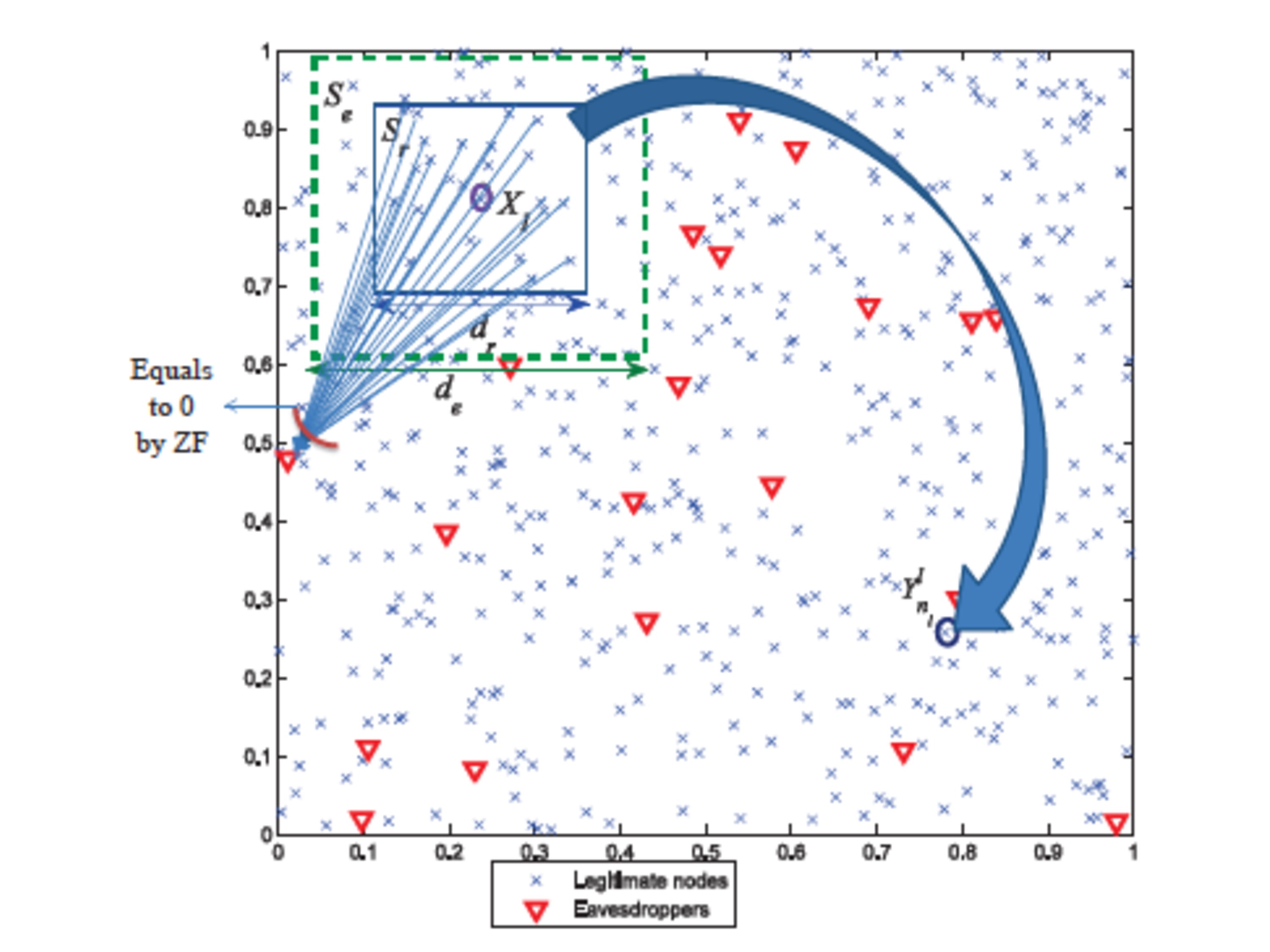
We have investigated a gamut of interesting problems leveraging information theoretic tools, inspired primarily from realistic systems settings. For example, using mobility as a source of common randomness, we established that a mobile infrastructure and a user/device could generate a shared cryptographic key on the fly, and essentially for free, during an average commute. Or, inspired by earlier research on communication across diverse paths, we created a novel information theoretic model for an active adversary (when the large majority of results is concerned with passive eavesdroppers). Or, motivated by recent developments in 4G systems, we investigated the scaling laws of secrecy preserving cooperative relaying.
Still, a fundamentally theoretical result, yet one that indicates that secure communication can be practically achieved at zero cost (for a fixed power constraint for the entire network).
Representative publications
| [1] | M. Mirmohseni and P. Papadimitratos, “Secrecy Capacity Scaling in Large Cooperative Wireless Networks,” IEEE Transactions on Information Theory (IEEE IT), vol. 63, no. 3, pp. 1923--1939, March 2017. [ bib | DOI | Full Text ] |
| [2] | P. Babaheidarian, S. Salimi, and P. Papadimitratos, “Security in the Gaussian Interference Channel: Weak and Moderately Weak Interference Regimes,” in IEEE International Symposium on Information Theory (IEEE ISIT), Barcelona, Spain, July 2016, pp. 2434--2438. [ bib | DOI | Full Text ] |
| [3] | M. Wiese and P. Papadimitratos, “Frequency Hopping does not Increase Anti-Jamming Resilience of Wireless Channels,” in International Zurich Seminar on Communications (IZS), Zurich, Switzerland, March 2016. [ bib | DOI | Full Text ] |
| [4] | P. Babaheidarian, S. Salimi, and P. Papadimitratos, “Finite-SNR Regime Analysis of the Gaussian Wiretap Multiple-Access Channel,” in IEEE Allerton Conference on Communication, Control, and Computing (IEEE Allerton), Monticello, IL, USA, September 2015, pp. 307--314. [ bib | DOI | Full Text ] |
| [5] | M. Mirmohseni and P. Papadimitratos, “Active Adversaries from an Information-Theoretic Perspective: Data Modification Attacks,” in IEEE International Symposium on Information Theory (IEEE ISIT), Honolulu, HI, USA, June 2014, pp. 791--795. [ bib | DOI | Full Text ] |
Secure and Reliable Communication
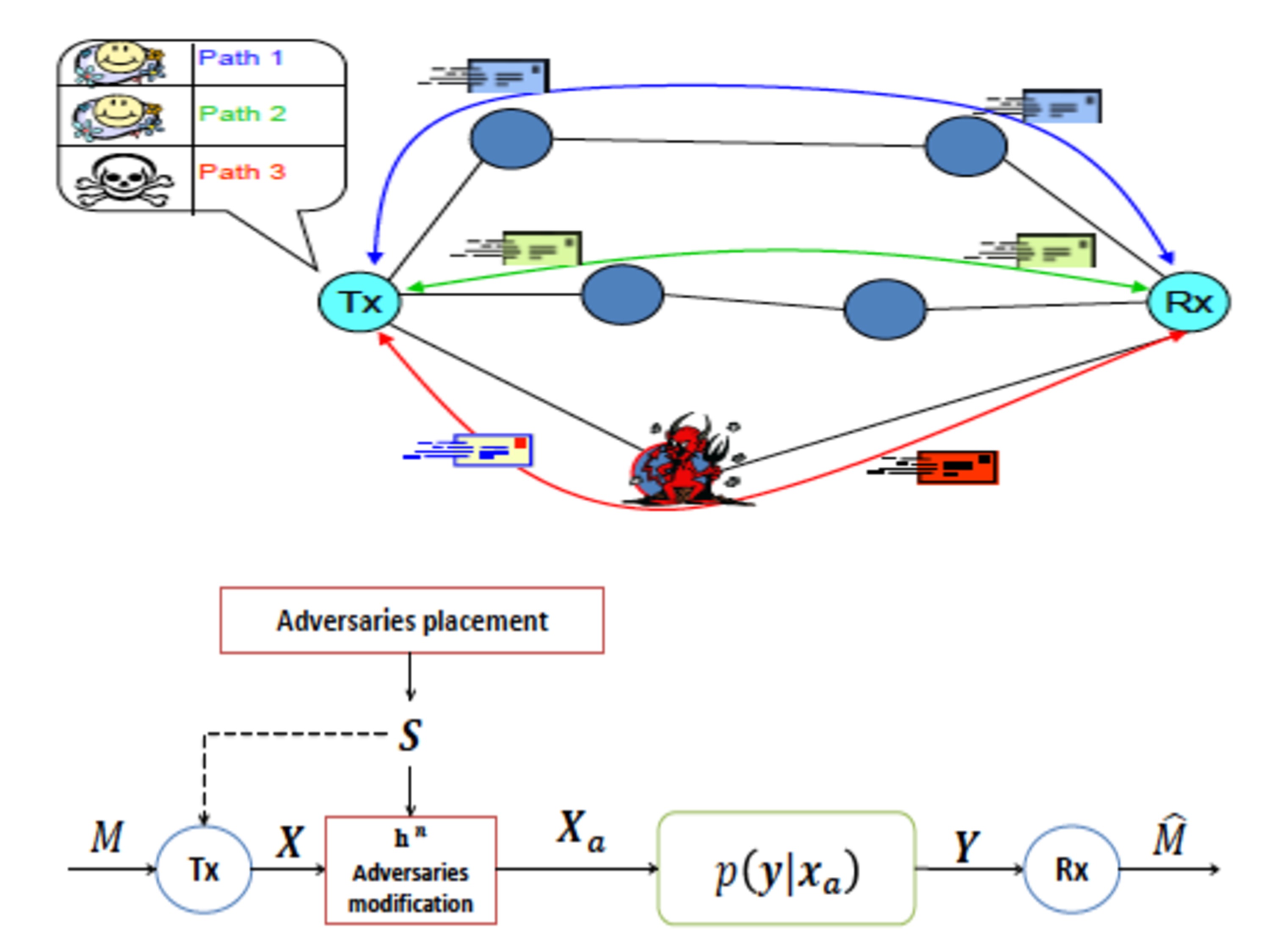
Our early work resulted in various security mechanisms for various types of route discovery. Secure routing alone cannot guarantee secure communication: An adversary could attack (e.g., drop packets) once it becomes part of a route. The overall problem was addressed by a secure and fault-tolerant communication protocol suite that does not require a priori knowledge of the trustworthiness of relaying nodes or the network dynamics. Towards systematic understanding of secure routing protocols, we developed a classification for a wide range of routing protocols.
More so, a routing specification that captures the essential features of highly volatile networking environments and enables formal analysis of candidate solutions. Revisiting the topic, a later approach of ours merged route discovery and data communication and new adaptive mechanisms, with enhanced scalability. More recently, we proposed a block-chain based approach to facilitate trust bootstrapping for interdomain Internet routing.
Representative publications
| [1] | A. de la Rocha and P. Papadimitratos, “Blockchain-based Public Key Infrastructure for Inter-Domain Secure Routing,” in IFIP WG 11.4 Workshop on Open Problems in Network Security (IFIP iNetSec), Rome, Italy, May 2017. [ bib | DOI | Full Text ] |
| [2] | M. Hollick, C. Nita-Rotaru, P. Papadimitratos, A. Perrig, and S. Schmid, “Toward a Taxonomy and Attacker Model for Secure Routing Protocols,” ACM SIGCOMM Computer Communication Review, vol. 47, no. 1, pp. 43--48, January 2017. [ bib | DOI | Full Text ] |
| [3] | W. Galuba, P. Papadimitratos, M. Poturalski, K. Aberer, Z. Despotovic, and W. Kellerer, “Castor: Scalable Secure Routing for Ad Hoc Networks,” in IEEE Conference on Computer Communications (IEEE INFOCOM), San Diego, CA, USA, March 2010, pp. 1--9. [ bib | DOI | Full Text ] |
| [4] | P. Papadimitratos and Z. Haas, “Secure Data Communication in Mobile Ad Hoc Networks,” IEEE Journal on Selected Areas in Communications (IEEE JSAC), vol. 24, no. 2, pp. 343--356, February 2006. [ bib | DOI | Full Text ] |
| [5] | P. Papadimitratos and Z. J. Haas, “Secure Routing for Mobile Ad Hoc Networks,” in SCS Communication Networks and Distributed Systems Modeling and Simulation Conference (CNDS), San Antonio, TX, USA, January 2002, pp. 193--204. [ bib | Full Text ] |
Research areas
Credential Management for Networked Systems
Security and Privacy for Location Based Services
Security and Privacy for Participatory Sensing Systems
Secure and Privacy Preserving Vehicular Networking
Information Theoretic Security
Notes
- - Only a part of the work is presented for now. Additional summaries will be added as soon as possible.
- - Please see the lists of publications and presentations for more information.
- - You are welcome to contact Prof. P. Papadimitratos via email (papadim@kth.se) with any questions or remarks.